Part 6 - Beyond Passwords: Strengthening Security with Zero Trust and Phishing-Resistant Authentication
Introduction
This is the final instalment of our six-part series on phishing attacks and defences. Part 1 provided an overview of the series, Part 2 explored various phishing attack types, Part 3 examined advanced phishing frameworks, our bonus content delved into post-exploitation techniques, Part 4 covered comprehensive protection strategies, and Part 5 explored detection with Microsoft Sentinel.
Throughout this series, we've examined increasingly sophisticated phishing attacks that can bypass traditional defences and even compromise standard multi-factor authentication. As we've seen, when prevention and detection fail, having strong mitigation controls becomes essential to limiting the damage attackers can cause.
In this final instalment, we'll explore how to implement a comprehensive Zero Trust approach to phishing mitigation through robust conditional access policies and phishing-resistant authentication methods. By combining these powerful controls, organisations can significantly reduce the risk posed by even the most advanced phishing techniques.
Conditional Access Fundamentals
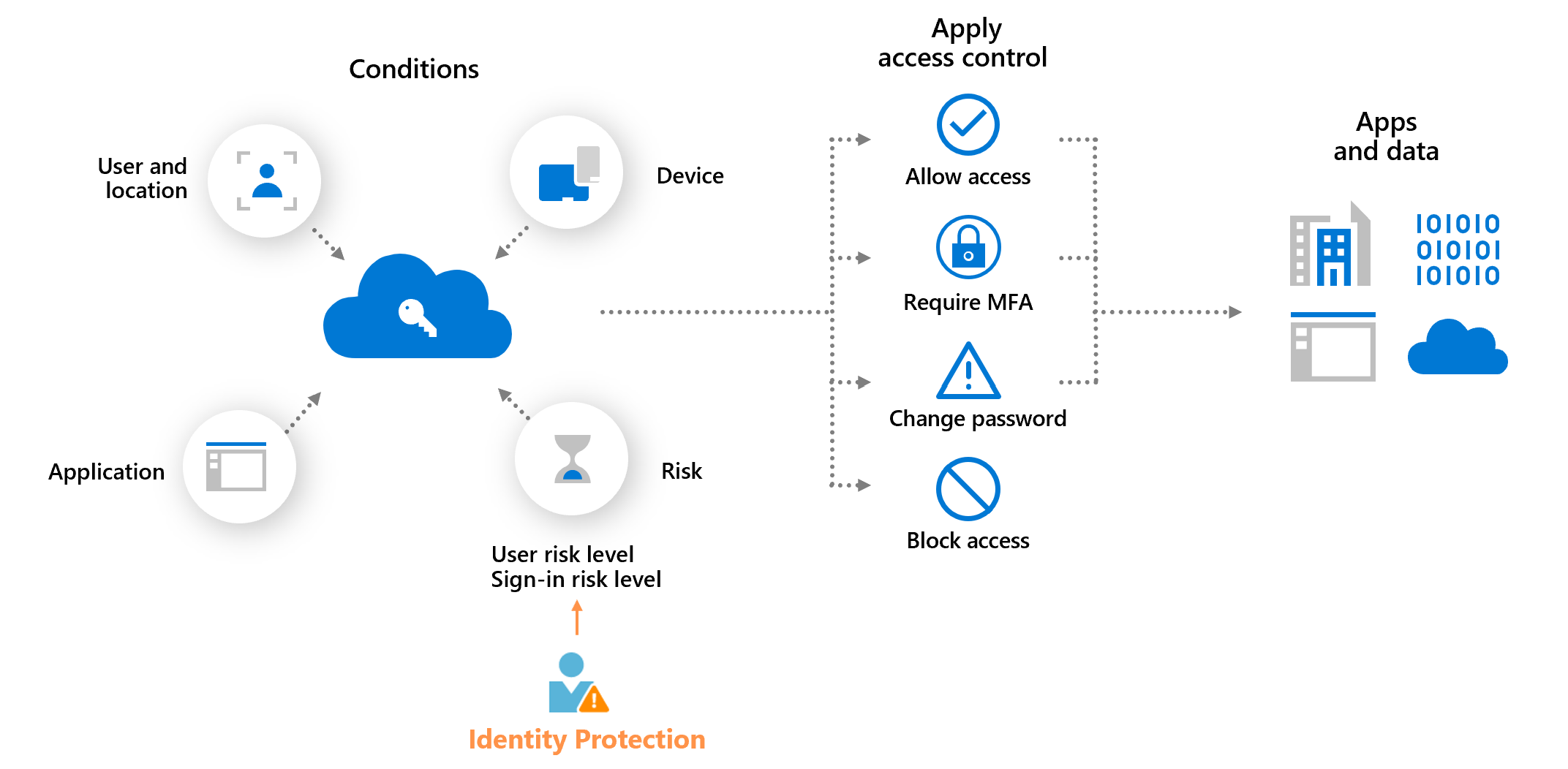
Conditional Access serves as the policy enforcement engine for Zero Trust, allowing organisations to make granular access decisions based on multiple signals rather than relying solely on traditional perimeter defences.
Zero Trust Principles for Authentication
The Zero Trust security model fundamentally changes how we approach security. Rather than assuming everything behind the corporate firewall is safe, Zero Trust requires explicit verification for every access request, regardless of where it originates. For authentication, this means verifying not just credentials, but also evaluating the context of each sign-in attempt.
The core principles include verifying explicitly by authenticating and authorising based on all available data points, using least privilege access to limit what users can reach, and assuming breach by minimising potential damage through segmentation and continuous verification. Conditional Access operationalises these principles by evaluating signals, enforcing policies, and making real-time access decisions.
Signal Evaluation in Conditional Access
Conditional Access evaluates a rich tapestry of signals when making access decisions. It examines user identity and group membership to apply role-appropriate policies. Device state signals include whether the device is managed, compliant with security policies, or flagged as risky. Location information helps identify access attempts from unusual or high-risk regions. The system also considers which application is being accessed and its sensitivity level.
Real-time risk detection signals flag potentially compromised accounts or suspicious sign-in patterns. When integrated with Microsoft Defender for Cloud Apps, Conditional Access can also incorporate cloud app risk assessments and apply specialised session controls.
Policy Enforcement Options
Based on the evaluation of these signals, Conditional Access can take several actions. It might block access entirely when risk indicators suggest a potentially compromised account. Alternatively, it can grant access, possibly with additional requirements such as re-authentication or approval. For scenarios where complete blocking isn't appropriate, session controls limit what users can do during authenticated sessions. Meanwhile, Continuous Access Evaluation ensures that access can be revoked immediately if risk conditions change.
Phishing-Resistant Authentication
Traditional password-based authentication and even standard MFA solutions can be compromised through sophisticated phishing. Phishing-resistant authentication provides stronger protection by design.
What Makes Authentication Phishing-Resistant?
The hallmark of phishing-resistant authentication is that it cannot be easily intercepted, stolen, or replicated by attackers. According to Microsoft's latest guidance, truly phishing-resistant methods incorporate cryptographic binding to legitimate service origins, ensuring that authentication responses work only with the genuine website they were created for. They store credentials in protected hardware elements, preventing extraction even if a device is compromised. Finally, they eliminate shared secrets like passwords or one-time codes that could be intercepted.
Microsoft Entra ID supports three primary forms of phishing-resistant authentication: FIDO2 security keys and passkeys, certificate-based authentication, and Windows Hello for Business. Each offers strong protection against credential theft while providing varying levels of user convenience.

FIDO2 Security Keys and Passkeys
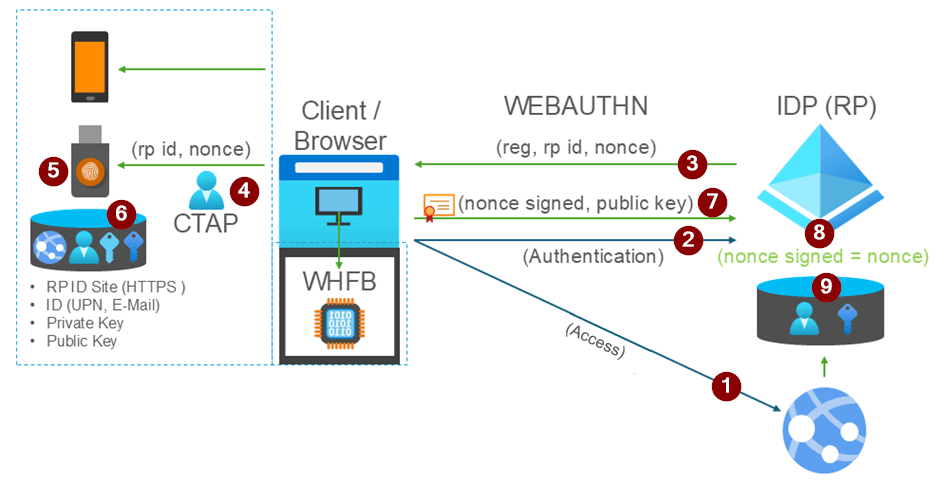
FIDO2 represents a significant advancement in authentication security. The standard uses public-key cryptography where a private key remains securely on the authenticator device, never shared with the service. When a user signs in, the service challenges the authenticator to prove possession of the private key without actually transmitting it.
The WebAuthn protocol within FIDO2 establishes secure communication between websites and authenticators, whilst the Client-to-Authenticator Protocol (CTAP) enables external security keys to communicate with browsers and platforms. Crucially, FIDO2 implements origin binding, cryptographically ensuring that credentials created for one website cannot be used for another—making phishing practically impossible.
For those interested in the technical underpinnings of FIDO2, Michael Waterman provides an excellent in-depth exploration of how this authentication standard functions at a detailed level. His analysis covers the cryptographic principles that make FIDO2 resistant to common attack vectors and explains why the architecture provides such strong protection against credential theft and phishing attempts. Whether you're implementing FIDO2 in your organisation or simply want to understand the security guarantees behind passkeys, this technical deep dive offers valuable insights into the protocols and mechanisms that keep your digital identity secure.
Passkeys: The Evolution of Authentication
Passkeys represent the next evolution of FIDO2, addressing many usability challenges that hindered widespread adoption of security keys. They provide cross-device authentication, allowing users to sign in to services on new devices using credentials stored on their phone or in cloud-synchronised password managers.
This cloud synchronisation creates secure backup options, resolving the recovery problems associated with physical security keys. Passkeys work across multiple platforms, including Windows, macOS, iOS, and Android, with broad browser support. The improved user experience relies on familiar biometric mechanisms like fingerprint readers or facial recognition, making strong authentication intuitive for users.
Implementing Phishing-Resistant Authentication with Entra ID
Microsoft has significantly streamlined the process for deploying phishing-resistant authentication. Let's look at the key implementation steps and considerations.
Prerequisites and Planning
Before implementing phishing-resistant authentication in your organisation, ensure you have the proper licensing—Microsoft Entra ID P1 or P2 for conditional access policies. You'll need to enable the FIDO2 security key method in your Entra ID tenant and ensure your network configuration allows access to WebAuthn protocol endpoints.
When planning your deployment, identify high-value targets first, such as privileged administrators, finance personnel, and executives who access sensitive information. These users benefit most from enhanced authentication security and present the greatest risk if compromised.
Device compatibility is another important consideration. For FIDO2 security keys, validate that your chosen hardware meets certification requirements and functions with your organisation's browsers and operating systems. For passkeys and Windows Hello for Business, assess your device estate to determine readiness and create a migration plan for incompatible systems.
Enabling FIDO2 and Passkeys in Entra ID
Enabling FIDO2 security keys in Entra ID is straightforward. Navigate to the Authentication methods section in your Entra ID portal, select FIDO2 Security Key, and enable the feature for your target users. You can select specific user groups or enable it for everyone.
For passkeys, the process is similar but requires enabling both the Microsoft Authenticator method and the FIDO2 options. Recent updates to Microsoft Authenticator allow it to function as a passkey provider, creating a seamless experience for mobile users.
Registration and User Onboarding
User onboarding requires careful planning and communication. For security keys, users must physically register their device through the Entra ID My Profile page. This process involves inserting the security key when prompted and following the device-specific instructions for biometric registration or PIN setup.
For passkey registration, users can create passkeys through the Authenticator app or directly in supported browsers. Microsoft has significantly improved this experience; users are guided through passkey creation with clear visual instructions and verification steps.
Temporary Access Pass: Streamlining Adoption
One of the practical challenges in deploying phishing-resistant authentication is the bootstrap problem: how do users securely register for passwordless methods without first using potentially vulnerable credentials?
Microsoft's Temporary Access Pass (TAP) solves this elegantly. A TAP is a time-limited passcode that administrators can generate for users, allowing secure authentication for initial onboarding or recovery scenarios. The TAP can be configured to work just once or for a limited period, providing a secure pathway to register phishing-resistant credentials without exposing permanent passwords.
To implement a TAP, administrators use the Entra ID portal to generate a temporary code for the user. This code can be securely communicated through an out-of-band channel, and the user then uses it to sign in and register their authentication methods. This approach eliminates the need for password reset processes that could be vulnerable to social engineering.

Enforcing Advanced Authentication with Conditional Access
Combining conditional access with phishing-resistant authentication creates a powerful defence against even the most sophisticated phishing attacks. Here are some effective implementation approaches.
Securing Privileged Access
For privileged accounts with administrative rights, implement strict policies requiring phishing-resistant authentication for all access. Target these policies at administrator roles and sensitive management applications. The policy should apply regardless of device compliance or network location, ensuring that privileged access always requires the strongest authentication.
This approach creates a security boundary around your most sensitive identities, ensuring that even if an attacker obtains credentials, they cannot proceed without physical access to the security key or registered biometric device.

Graduated Implementation for General Users
For general users, consider a graduated implementation that balances security with user experience. Begin by requiring phishing-resistant authentication under higher-risk conditions, such as accessing from unmanaged devices or from unfamiliar locations. As users become comfortable with the new methods, you can expand the policy to cover more scenarios.
A sensible approach might require passwordless authentication when device compliance status is unknown or when connecting from outside the corporate network. This protects against the most common attack scenarios while allowing flexibility within managed environments.
Risk-Based Conditional Access
Microsoft's identity protection features detect potentially risky sign-ins based on user behaviour anomalies and known attack patterns. By integrating risk assessments with authentication requirements, you can dynamically adjust controls based on suspicious activity.
Configure policies that require phishing-resistant authentication when medium or high user risk is detected. This creates an adaptive security posture, elevating security requirements only when necessary. During normal operations, users enjoy a streamlined experience, but suspicious patterns trigger stronger verification—an excellent balance of security and usability.
Application-Specific Protection
Certain applications warrant heightened protection due to the sensitivity of their data. Financial systems, human resources applications, and intellectual property repositories often contain your organisation's most valuable information.
Design application-specific policies that require phishing-resistant authentication regardless of other contextual factors. This approach ensures that access to your crown jewels always requires strong verification, whilst possibly allowing more flexibility for less sensitive applications.
Session Controls for Additional Protection
Session controls represent a critical component in your defense-in-depth strategy, functioning as guardrails even after authentication succeeds. As detailed in John Savill's analysis of continuous authorization, organisations can implement tiered session policies based on authentication strength. Beyond authentication, session controls add another layer of protection by limiting what users can do after authentication. For sessions authenticated with standard methods, you might implement shorter timeouts, restrict download capabilities, or enable continuous access evaluation. These controls reduce the window of opportunity for attackers who manage to compromise credentials. For sessions authenticated with phishing-resistant methods, you might apply more lenient session policies, creating a positive incentive for users to adopt the stronger methods. This risk-based approach not only enhances security but also creates a natural pathway toward broader adoption of phishing-resistant authentication.

Measuring Effectiveness and Continuous Improvement
Implementing advanced authentication and conditional access is not a one-time project but a continuous improvement cycle.
Monitoring Policy Impact
Once your policies are in place, monitor their effectiveness through Entra ID's rich reporting capabilities. Track authentication success and failure rates to identify potential issues or user adoption barriers. Review help desk tickets related to authentication to spot recurring problems.
Analyse policy trigger frequency to understand how often each condition is met and which policies have the greatest impact. Monitor any exclusions to identify potential security gaps, and regularly review authentication method analytics to track adoption of phishing-resistant methods.

User Experience Considerations
The success of any security initiative depends heavily on user acceptance. Prepare users for new authentication requirements through clear communication and training materials. Consider a gradual rollout to manage change effectively and establish feedback channels for users to report issues.
Enable self-service options whenever possible, allowing users to resolve common problems like registering new devices or resetting authentication methods. Prepare your support team with troubleshooting tools and knowledge to efficiently assist users with authentication challenges.
Adapting to Emerging Threats
As we've seen throughout this series, phishing techniques constantly evolve. Stay ahead of these changes by integrating threat intelligence into your policy design. Regularly test your defences through simulated phishing campaigns targeting your new authentication methods.
Industry collaboration provides valuable insights into emerging attack vectors. Participate in security communities and work with vendors on strengthening your defences. Keep your security team current on phishing trends and technological countermeasures through continuous education.
Conclusion: The Future of Phishing Defence
As we conclude this series, it's clear that effective phishing defence requires a comprehensive approach spanning prevention, detection, and mitigation. While sophisticated attacks will continue to evolve, the combination of modern email security, advanced detection capabilities, phishing-resistant authentication, and robust conditional access policies creates a formidable defence against even the most determined adversaries.
By implementing the strategies covered throughout this series, organisations can significantly reduce their vulnerability to phishing and limit the impact when attacks inevitably occur. Most importantly, these approaches operationalise Zero Trust principles in practical ways that balance security with user experience and business needs.
I hope this series has provided valuable insights and practical guidance for strengthening your organisation's defences against phishing. I look forward to discussing these topics further at my upcoming presentation at the Microsoft 365 Community Conference in Las Vegas on 6-8 May 2025.
What aspects of conditional access and phishing-resistant authentication have you implemented in your organisation? Share your experiences and questions in the comments below.
This concludes our six-part series on phishing attacks and defences. If you missed any previous instalments, I encourage you to explore Part 1: Introduction to the Blog Series, Part 2: Understanding Modern Phishing Attacks, Part 3: Inside the Attacker's Toolkit, our bonus content on token theft, Part 4: Comprehensive Phishing Defences, and Part 5: Finding the Compromised with Microsoft Sentinel.
I hope you've found this guide helpful in enhancing your security posture. If you've enjoyed this content and would like to support more like it, please consider joining the Supporters Tier. Your support helps me continue creating practical security automation content for the community.






