Part 2 - The Phishing Threat Landscape: Understanding Attack Types and Techniques
Beyond the Bait: Navigating the Evolving Maze of Modern Phishing Tactics
Introduction
This is Part 2 of our six-part series on phishing attacks and defences. Part 1 provided an overview of the series and why understanding phishing is critical for modern security programmes.
Phishing remains one of the most prevalent attack vectors worldwide. Despite growing awareness, these attacks succeed by targeting human psychology—exploiting trust, creating urgency, and bypassing technical controls. This article examines the types of phishing attacks organisations face today and their evolving tactics.
The Financial Impact of Phishing
The business impact of phishing attacks has reached unprecedented levels in recent years. According to multiple industry reports:
In 2024, the global average cost of a data breach, including those resulting from phishing attacks, reached a staggering £3.76 million ($4.88 million), a 10% increase from the previous year. This highlights the significant financial impact these cyber threats pose to organisations of all sizes.
Phishing's role in data breaches is substantial, accounting for 15% of all reported attacks that resulted in breaches, each with that same average cost of £3.76 million ($4.88 million) per incident. When broken down by attack type:
- Business Email Compromise (BEC) attacks, which typically involve sophisticated phishing techniques, cost organisations an average of £3.60 million ($4.67 million) per incident
- Social Engineering attacks, which frequently leverage phishing tactics, result in average costs of £3.67 million ($4.77 million) per incident
The financial toll extends beyond immediate incident response. According to Keepnet Labs, businesses lose approximately £13,629 ($17,700) per minute due to phishing attacks when considering the full scope of impact, which includes:
- Lost productivity and operational downtime
- Reputational damage leading to customer attrition and reduced brand trust
- Legal and regulatory costs stemming from data protection violations
- Increased cyber insurance premiums following incidents
The emergence of AI-powered phishing tools has further complicated the landscape, making these attacks more sophisticated and increasingly difficult to detect, thereby elevating both risk and potential costs for targeted organisations.
The Evolution of Phishing Attacks
Today's phishing attacks are sophisticated, targeted, and often indistinguishable from legitimate communications—a far cry from the obvious "Nigerian prince" emails of the 1990s.
While mass campaigns still occur, many threat actors now use precision targeting, researching potential victims and crafting personalised messages. Modern attacks frequently leverage compromised accounts and trusted relationships, defeating traditional security measures.
Phishing has also expanded beyond email to multiple channels:
- Text messages
- Social media platforms
- Messaging applications
- Voice calls
- QR codes
- Search engine advertisements
This multi-channel approach increases success rates and complicates defensive strategies.
Types of Phishing Attacks
Understanding the various phishing methods helps organisations develop appropriate defences and training programmes. Let's explore the most common types of phishing attacks and their distinguishing characteristics.
Email Phishing (Deceptive Phishing)
The most prevalent form, email phishing involves sending deceptive emails that appear to come from trusted sources. These messages typically contain:
- Urgent calls to action
- Links to fraudulent websites that mimic legitimate ones
- Attachments containing malware
- Requests for sensitive information
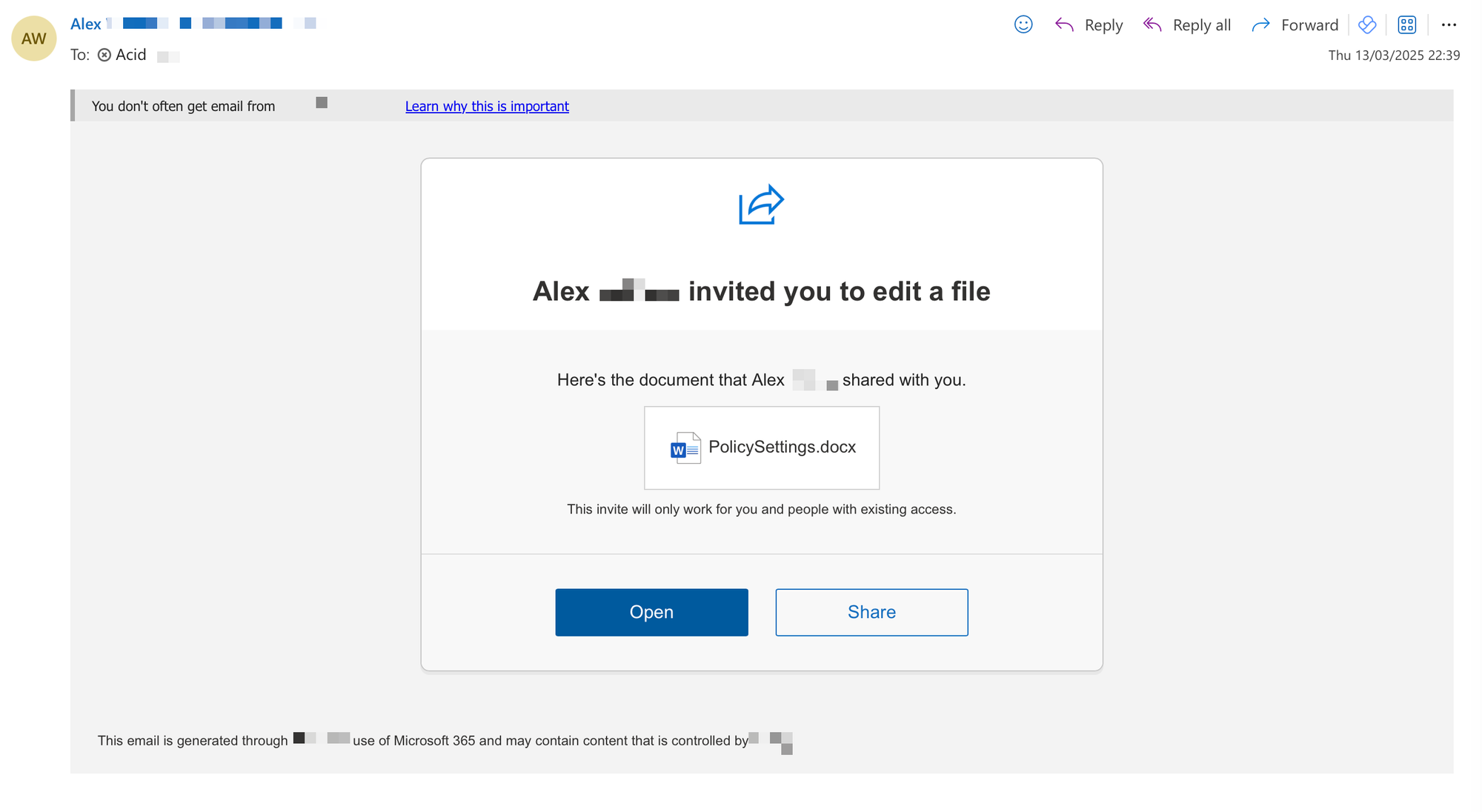
Example scenario: An email appearing to come from a colleague named "Alex" invites the recipient to edit a document titled "PolicySettings.docx" with Microsoft 365 branding. The email contains the standard elements of a file-sharing notification, including "Open" and "Share" buttons. However, clicking these buttons would likely lead to a credential harvesting page designed to steal Microsoft 365 login information. The email includes subtle warning signs such as the "You don't often get email from" banner that Microsoft adds to unfamiliar senders, but many recipients might overlook this in their haste to access what appears to be an important policy document.
Spear Phishing (Targeted Phishing)
Unlike general email phishing, spear phishing targets specific individuals or organisations with highly personalised messages. Attackers research their victims beforehand, often incorporating:
- Personal details gathered from social media or data breaches
- References to colleagues or managers
- Mention of specific projects or events
- Company-specific terminology
- Industry-relevant topics
Example scenario: A financial controller receives an email that appears to be from their CEO (using their actual name and email format), requesting an urgent wire transfer for a confidential acquisition, referencing an actual company project discussed in a recent board meeting.
Whaling (Executive Phishing or CEO Fraud)
Whaling specifically targets high-profile executives or other high-value targets within an organisation. These attacks require extensive research and are meticulously crafted to appear legitimate to busy executives who may have less time to scrutinise messages.
Example scenario: A CFO receives what appears to be a legitimate invitation to review an acquisition proposal via a secure document sharing site, which actually captures their corporate credentials and uses them to initiate fraudulent payments.
Smishing (SMS Phishing)
Smishing uses SMS or text messages to deceive recipients. These messages often contain:
- Shortened URLs to mask malicious destinations
- Urgent notifications about accounts, deliveries, or payments
- Impersonation of well-known brands or services
- Exploitation of current events or concerns
Example scenario: A user receives a text message claiming to be from Royal Mail, stating that a delivery attempt failed and they need to reschedule by clicking a provided link, which leads to a credential harvesting page or malware download.
Vishing (Voice Phishing or VoIP Phishing)
Vishing involves phone calls from scammers posing as legitimate entities. These calls often:
- Create a sense of urgency or fear
- Impersonate trusted organisations like banks, tax authorities, or tech support
- Use caller ID spoofing to appear legitimate
- Combine with other phishing methods as part of a multi-channel attack
Example scenario: An employee receives a call from someone claiming to be from their IT helpdesk, stating they've detected suspicious activity from the employee's account and need their credentials to "secure" the system.
Business Email Compromise (BEC or Email Account Compromise)
BEC attacks involve compromising or impersonating business email accounts to conduct unauthorised fund transfers or access sensitive data. These sophisticated attacks often:
- Target financial departments or personnel with payment authority
- Modify legitimate payment instructions to redirect funds
- Create convincing domains that closely resemble legitimate ones
- Exploit trusted business relationships and expected transactions
Example scenario: A supplier's email account is compromised, and the attacker monitors communications until an invoice is due. They then send altered payment instructions from the legitimate email account, redirecting payment to their own account.
Clone Phishing (Email Replication Attacks)
Clone phishing replicates legitimate emails previously sent from trusted sources but replaces attachments or links with malicious versions. The attacker often claims to be "resending" or providing an "updated version" of a previous communication.
Example scenario: An employee receives what appears to be a resend of a legitimate HR document they received earlier, with a message saying, "Sorry, the previous version had errors. Please use this updated form instead." The new attachment contains malware.
Pharming (DNS Poisoning)
Pharming attacks involve redirecting users from legitimate websites to fraudulent ones through DNS hijacking or poisoning. Unlike traditional phishing that relies on users clicking malicious links, pharming can happen even when users correctly type a website's address.
Example scenario: Attackers compromise a company's DNS settings so that when employees try to access the legitimate company portal by typing its correct URL, they're redirected to a visually identical but fraudulent site that captures their login credentials.
Angler Phishing (Social Media Phishing)
Angler phishing targets users on social media platforms by impersonating customer service accounts of well-known companies. When users complain about a company's service on social media, attackers respond posing as support staff and direct victims to fraudulent sites.
Example scenario: A customer tweets a complaint about their bank's mobile app. A fraudulent account with a similar name to the bank's official support account responds with a link to a "secure form" where they can "verify their identity" to receive help.
Search Engine Phishing (SEO Poisoning)
This technique involves manipulating search engine results to lead users to malicious websites. Attackers optimise fraudulent websites to rank highly for specific search terms, particularly those related to banking, online shopping, or technical support.
Example scenario: A user searches for "reset Amazon password" and clicks on a high-ranking result that leads to a convincing but fraudulent Amazon login page designed to steal credentials.
QR Code Phishing (Quishing)
QR code phishing, or "quishing," uses malicious QR codes to direct victims to phishing websites. These codes can be placed on physical materials like flyers, posters, or stickers, or sent digitally in emails or messages.
Example scenario: An employee receives an email about a new company benefit programme with a QR code to "register quickly from your phone." The code directs them to a site that mimics the company's intranet but steals their corporate credentials.

Zombie Phishing (Account Takeover Phishing)
Zombie phishing occurs when attackers compromise email accounts and then use them to launch phishing campaigns from previously dormant or "dead" email threads. This technique is particularly effective because:
- The emails come from legitimate, trusted accounts
- Attackers often reply to existing email threads
- Recipients are more likely to engage with what appears to be a continuation of previous legitimate conversations
Example scenario: A contractor's email account is compromised but not immediately used. Months later, the attacker reviews old email threads and responds to a previous discussion about invoice payments, attaching a malicious "updated invoice template" that contains malware.
Social Engineering Tactics in Phishing
Effective phishing relies heavily on social engineering—psychological manipulation techniques that exploit human behaviour and emotions. Understanding these tactics can help organisations better prepare their staff to recognise and resist phishing attempts.
Creating Urgency
One of the most common tactics is creating a false sense of urgency that pressures victims into acting quickly without thoroughly evaluating the situation. Messages might claim accounts will be closed, payments missed, or opportunities lost unless immediate action is taken.
Authority Exploitation
Phishing often impersonates authority figures or trusted institutions—banks, government agencies, executives, IT departments—to increase the likelihood of compliance. People are naturally inclined to respond to requests from perceived authorities.
Fear Manipulation
Many phishing attempts generate fear or anxiety to override rational thinking. Warnings about security breaches, fraudulent charges, or account suspensions create emotional responses that can lead to hasty actions.
Curiosity Triggers
Some phishing messages exploit natural curiosity with intriguing subject lines or content that promises interesting information, exclusive offers, or attention-grabbing news.
Trust Relationships
By compromising legitimate accounts or impersonating known contacts, phishers exploit existing trust relationships to increase their success rates. People are far more likely to click links or open attachments from someone they know and trust.
Signs of a Phishing Attempt
While phishing attacks grow increasingly sophisticated, they often contain subtle indicators that can help alert recipients to potential threats:
Email and Message Indicators
- Mismatched or suspicious URLs (hover before clicking to preview the actual destination)
- Generic greetings instead of personalised ones
- Grammatical errors or awkward phrasing (though sophisticated attacks often eliminate these)
- Email domains that closely resemble legitimate ones but contain subtle differences
- Unexpected attachments, especially executable files or password-protected archives
- Requests to disable security features or enable macros
Content and Context Red Flags
- Requests for sensitive information that would not normally be solicited via that channel
- Unexpected communications about accounts, deliveries, or payments
- Offers that seem too good to be true
- Appeals to urgency or threats of negative consequences
- Content that doesn't align with the purported sender's typical communication style
Technical Warning Signs
- Links that redirect through multiple domains
- Websites lacking expected security certificates or showing certificate warnings
- Forms requesting excessive personal or financial information
- URLs with unusual TLDs (top-level domains) or character substitutions
- Suspicious sender information when examining full email headers
The Impact of Successful Phishing
Understanding the potential consequences of successful phishing attacks helps organisations appreciate the importance of comprehensive defences:
Initial Compromise
- Credential theft leading to account takeovers
- Malware installation providing persistent access
- Data theft of personal, financial, or proprietary information
- Financial fraud through redirected payments or fraudulent transactions
Secondary Exploitation
- Lateral movement throughout the network
- Privilege escalation to gain administrative access
- Data exfiltration of sensitive corporate information
- Ransomware deployment affecting entire networks
- Long-term persistence and intelligence gathering
Conclusion: Building on This Knowledge
The variety and sophistication of phishing attacks can seem overwhelming, but understanding the threat landscape is the first critical step toward effective defence. By recognising the types of attacks, the psychological triggers they exploit, and their warning signs, organisations can begin building appropriate technological and human defences.
In Part 3 of our series, we'll take a deep dive into the sophisticated tools threat actors use to execute these attacks, with particular focus on frameworks that can bypass traditional multi-factor authentication. Understanding these tools is crucial for security professionals tasked with defending against modern phishing campaigns.
Following that, our special bonus content will explore the dangerous world of token theft and how initial phishing compromises can lead to persistent threats through stolen authentication tokens and cookies.
Have questions about specific phishing techniques or want to share an experience? Leave a comment below, and don't forget to subscribe for updates as this series continues.
This article is part of a six-part series (plus bonus content) on phishing attacks and defences. Read Part 1: Introduction to the Blog Series if you haven't already, and stay tuned for the upcoming instalments leading to my presentation at the Microsoft 365 Community Conference in Las Vegas on 6-8 May 2025.