Bonus - The Growing Threat of Token Theft: How Attackers Exploit Stolen Authentication After Successful Phishing

Introduction
This is special bonus content in our six-part series on phishing attacks and defences. Part 1 provided an overview of the series, Part 2 explored various phishing attack types, and Part 3 examined the advanced phishing framework Evilginx.
Successfully obtaining credentials through phishing is rarely the ultimate goal for threat actors—it's merely the beginning. Once attackers have initial access through phished credentials or stolen session tokens, they employ sophisticated techniques and tools to maintain persistence, escalate privileges, and move laterally through the compromised environment.
In this bonus instalment, we'll explore what the potential risks after a successful phishing attack when authentication tokens are captured. We'll examine how threat actors leverage these tokens to expand their access and the tools they use to exploit Microsoft 365 and Azure environments in particular.
Understanding Authentication Tokens
Before diving into post-exploitation techniques, it's important to understand what authentication tokens are and why they're increasingly targeted by attackers.
What Are Authentication Tokens?
Authentication tokens are digital credentials that verify user identity after initial login. Unlike passwords, tokens are automatically generated, have varying lifespans, and maintain sessions without repeated logins. They accompany each request to verify identity and are commonly stored as cookies or in application storage, making them accessible targets for attackers.
Types of Tokens in Modern Authentication
Cloud environments use multiple token types together. Session tokens maintain web sessions, while access tokens grant short-term resource access. Refresh tokens are particularly valuable as they generate new access tokens without re-authentication. ID tokens contain user identity information, SAML tokens support federated authentication, and OAuth tokens enable cross-service authorization – all becoming powerful tools when compromised.
Why Tokens Are Valuable to Attackers
Tokens offer attackers significant advantages. They bypass MFA challenges once obtained and many refresh tokens remain valid for 30-90 days, providing persistent access. Their integration across cloud services means compromising one token often grants access to multiple systems. Token-based access appears legitimate to security systems, generating fewer alerts than other attack methods. Additionally, tokens can be extracted from one device and used on another, giving attackers remarkable operational flexibility.
Token Capture Techniques
In Part 3, we explored how attackers obtain authentication tokens through Evilginx that act as reverse proxies during authentication. Beyond these dedicated phishing frameworks, attackers employ several additional methods: browser-based techniques that extract cookies from storage or memory; hooking attacks that capture tokens during generation; and full device compromise that provides complete access to all authentication mechanisms. While obtaining tokens represents the initial breach, what happens next—the exploitation phase—poses the greatest threat to organisations.
The Token Theft Toolkit: Post-Exploitation Tools
Once tokens are captured, attackers employ specialised tools to leverage them for expanded access. Let's examine a powerful and concerning tool in this category that specifically targets Microsoft 365 environments.
GraphRunner: Weaponising Microsoft Graph API
GraphRunner is a powerful post-exploitation tool designed to abuse Microsoft Graph API access for reconnaissance and lateral movement within Microsoft 365 environments. Developed by security researcher Beau Bullock (@dafthack), this open-source tool highlights the significant risks posed by compromised authentication tokens.
Technical Overview
GraphRunner is built in PowerShell and focuses specifically on automating Microsoft Graph API abuse. The tool is designed to be modular, discreet, and highly effective at mapping out and exploiting permissions available to a compromised identity.
Import-Module .\GraphRunner.ps1
Get-Help Invoke-GraphRunner
This simple command structure belies the tool's sophisticated capabilities, which can be executed with minimal noise in the target environment.
Token Acquisition and Usage
GraphRunner can obtain tokens through various methods that mirror legitimate authentication flows. It supports direct authentication using compromised credentials to obtain fresh tokens, seamlessly importing tokens captured from phishing frameworks like Evilginx, and leveraging device code authentication when available. The tool excels at using stolen refresh tokens to generate new access tokens, extending the compromise long after the initial attack. Some implementations even support pulling tokens directly from compromised browser sessions. Once a valid token is obtained, GraphRunner uses it to authenticate to the Microsoft Graph API, effectively assuming the identity and permissions of the compromised user without triggering security alerts.
AutoGraph: Streamlining Microsoft 365 Post-Exploitation
To demonstrate how easily GraphRunner can be weaponised, I created AutoGraph, an automation framework that significantly simplifies the post-exploitation process for attackers. This tool provides a user-friendly interface to GraphRunner's functionality, making sophisticated attacks accessible even to less technically skilled threat actors.
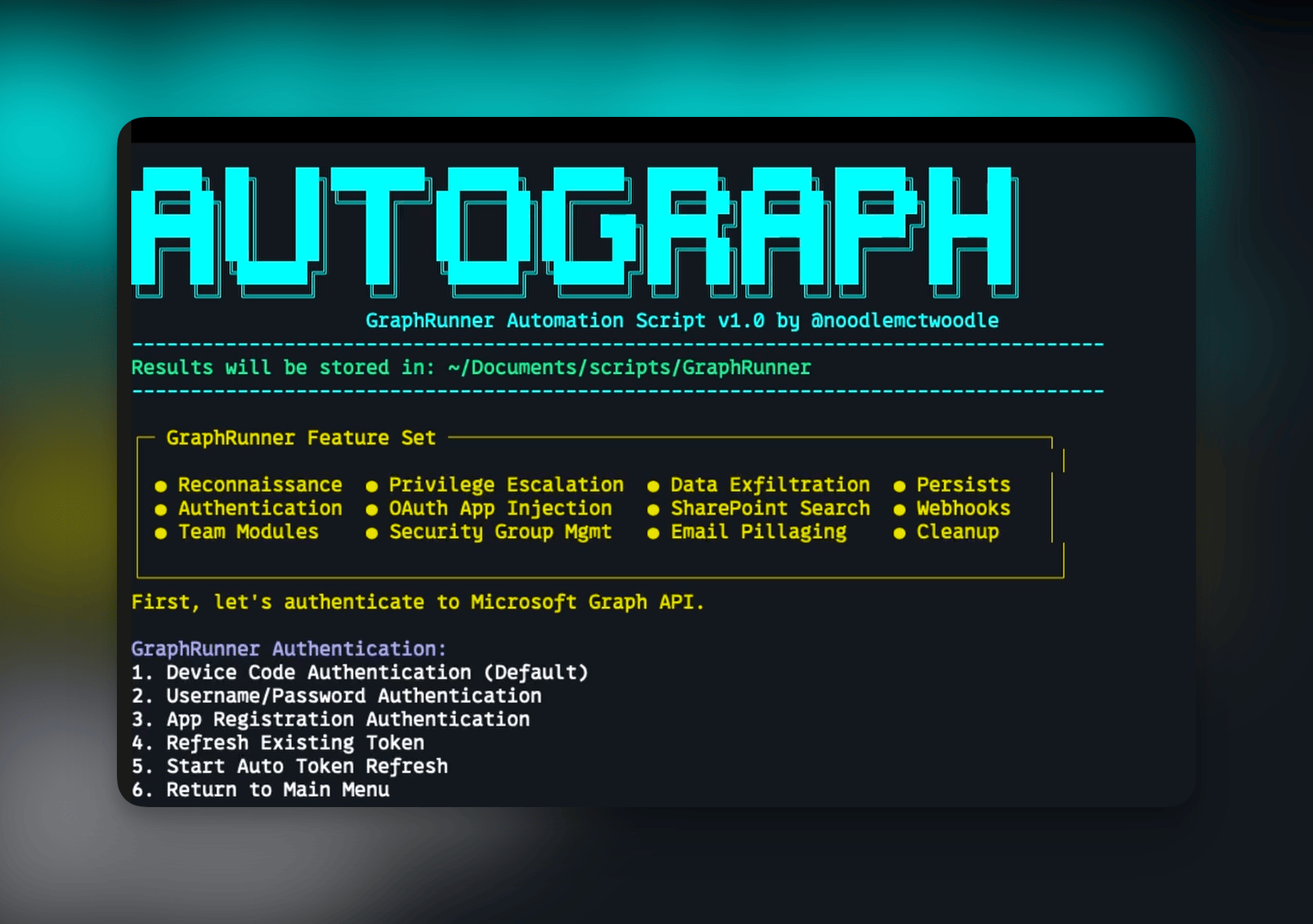
Key Features of AutoGraph
AutoGraph provides a menu-driven interface that transforms complex API interactions into simple menu selections. The tool manages authentication through multiple flows including device code, username/password, app registration, and token refresh, making it trivial to use stolen credentials or tokens. Its reconnaissance operations automate user enumeration, group mapping, and permission discovery, building a comprehensive map of the target organisation within minutes. The privilege escalation functions streamline dangerous techniques like OAuth app injection, security group cloning, and guest user invitation. For data theft, AutoGraph facilitates systematic searching and extraction of sensitive information from emails, SharePoint, OneDrive, and Teams. Perhaps most concerning are its persistence mechanisms, which implement mail forwarding rules and other techniques to maintain long-term access even after the initial compromise is discovered.
Automated Token Management
One of the most sophisticated aspects of AutoGraph is its automated token refresh capabilities. The tool continuously monitors token expiration and automatically refreshes tokens before they expire, handling different token formats and expiration representations with ease. It securely stores tokens for continued access and verifies their validity before each operation, intelligently managing refresh strategies based on different authentication types. This capability ensures that an attacker maintains persistent access even with short-lived access tokens, effectively bypassing the security benefit of token expiration policies.
Simplified Operational Security
AutoGraph implements several features that help attackers maintain operational security while conducting their campaigns. It incorporates clear error handling to prevent failed operations that might trigger security alerts and provides guided prompts for sensitive operations to prevent mistakes that could reveal the attacker's presence. The tool formats output for easier data analysis, automatically generates payloads for common attack techniques, and carefully manages output folders for organizing extracted data. These features reduce the technical skill required to conduct sophisticated attacks while minimizing the risk of detection.
Dangerous Applications of Graph API Abuse
The Microsoft Graph API provides a unified programmability model to access vast amounts of data in Microsoft 365 services. When weaponised through tools like GraphRunner and AutoGraph, it becomes an extremely powerful vector for reconnaissance and data theft. Let me highlight just two particularly dangerous capabilities that demonstrate why organisations need to carefully monitor API access.
Comprehensive Organisational Mapping
One of the most concerning capabilities is how quickly these tools can build a complete map of an organisation's structure. Within minutes, an attacker can obtain detailed information about all users in the tenant, including email addresses, contact information, department affiliations, job titles, and reporting relationships. The tools can automatically enumerate security groups, distribution lists, Microsoft 365 Groups, and their members, revealing the entire organisational structure.
This reconnaissance provides attackers with everything needed to understand potential targets, identify privilege escalation paths, and plan further attacks. The information gathered enables highly targeted social engineering, helps identify high-value targets based on their position, and reveals the relationships between users and groups that can be exploited for lateral movement.
Email Targeting and Data Exfiltration
Perhaps the most damaging capability is how these tools can systematically pillage email and document repositories. Attackers can silently search through mailboxes for sensitive keywords like "password," "confidential," or "financial," rapidly identifying valuable information. The tools can automatically download attachments, export entire email threads, and even create forwarding rules to maintain access to sensitive communications.
Similarly, they can inventory all SharePoint sites and OneDrive locations accessible to the compromised account, identify documents containing sensitive information, and exfiltrate them automatically. This targeted approach allows attackers to quickly locate and steal intellectual property, financial information, strategic plans, and other high-value data with minimal effort.
The Comprehensive Attack Surface
The scope of accessible data extends far beyond just emails and documents. These tools can extract valuable conversations and shared files from Microsoft Teams, revealing internal discussions about projects, shared files, meeting recordings, and chat histories containing potentially sensitive information. They can access calendar data to identify high-value meetings, obtain meeting join links for eavesdropping, and gather intelligence on business activities and relationships with external partners.
What makes these capabilities particularly dangerous is how they're tied together in tools like AutoGraph. Through a simple menu interface, even minimally skilled attackers can orchestrate comprehensive data theft operations across all Microsoft 365 services simultaneously. The automation streamlines what would otherwise be complex technical processes, allowing attackers to focus on identifying and extracting the most valuable information rather than struggling with API intricacies.
Advanced Exploitation Techniques
Beyond data theft, these tools enable sophisticated persistence techniques that allow attackers to maintain access even after the initial compromise is discovered and remediated.
Even more concerning is the ability to manipulate application registrations and service principals. Attackers can create what appear to be legitimate enterprise applications with names like "Microsoft Security Service" or "Azure Compliance Manager" that blend into the environment. These applications can be granted persistent API permissions that survive user password changes, effectively creating backdoor access that traditional remediation steps may miss. Since these applications use their own authentication flow, they provide attackers with a completely separate access path that doesn't depend on the originally compromised user account.
Defensive Challenges and Detection Opportunities
Tools like GraphRunner and AutoGraph present significant challenges for defenders. Since they use official Microsoft APIs, their activity can blend with normal business operations, making it difficult to distinguish from legitimate use. Unlike traditional malware, there's no payload to detect on endpoints, leaving no traces for traditional antivirus or EDR solutions to find. These tools leverage identity-based access that bypasses traditional network controls entirely, operating entirely within authenticated channels. The intricate permission model in Microsoft 365 makes it difficult to properly restrict access without impacting legitimate business functions. Perhaps most challenging is how the actions taken often mirror legitimate user activities, making behavioural detection complex.
However, several detection opportunities exist. These tools typically generate distinctive patterns of API calls that differ from normal user behaviour. The mass downloading of documents or emails creates detectable traffic spikes that can trigger volume-based alerts. Geographic inconsistencies, where API access originates from locations inconsistent with the user's normal pattern, can indicate compromise. "Impossible travel" scenarios, where API calls come from different geographic locations within unreasonable timeframes, are strong indicators of token theft. User agent anomalies can reveal tool usage, as GraphRunner and AutoGraph leave distinctive traces in user agent strings. Authentication anomalies, particularly token usage patterns that differ from normal user behaviour, can indicate compromise. Finally, unusually long or active sessions compared to typical user behaviour can reveal automated tool usage.
Advanced Defence Techniques
To counter these sophisticated post-exploitation tools, organisations need a layered defence strategy. Token lifetime policies should be implemented to reduce access token lifetimes and force more frequent reauthentication, complemented by conditional access policies that continuously reevaluate risk throughout active sessions. Comprehensive API activity monitoring through CASB or UEBA solutions can detect unusual API access patterns that might indicate tool usage.
Organisations should create conditional access policies that require reauthentication when risk factors are detected, such as access from new locations or unusual access patterns. Session controls like duration limits and mandatory reauthentication for sensitive operations can limit the damage from compromised tokens. Regular permission auditing helps minimise the access available to compromised accounts, following the principle of least privilege. API rate limiting can prevent the rapid API abuse typical of automated tools, while user entity behaviour analytics solutions can identify abnormal patterns in user authentication and API access before significant damage occurs.
Conclusion: Beyond the Initial Compromise
Token theft represents a critical evolution in the threat landscape, extending the impact of successful phishing attacks far beyond the initial compromise. Tools like GraphRunner and AutoGraph demonstrate the increasing sophistication and automation available to attackers, enabling even less skilled threat actors to conduct comprehensive breaches of Microsoft 365 environments.
By understanding how attackers leverage stolen tokens and the tools they use, security teams can better detect, contain, and respond to these sophisticated threats.
In Part 4 of our series, we'll explore comprehensive phishing protection strategies, including email authentication protocols, Microsoft Defender for Office 365 capabilities, and effective user awareness training approaches that can help organisations defend against these sophisticated attacks at their source. We'll also cover Microsoft's Automatic Attack Disruption capabilities, which can help organisations respond rapidly to detected threats.
We'll dive deeper into detection strategies in Part 5 - "Finding the Compromised: Microsoft Sentinel for Phishing Detection and Response," where we'll explore how to build effective detection rules for GraphRunner and Graph API abuse. We'll examine specific Microsoft Sentinel analytics rules that can identify suspicious API usage patterns, abnormal authentication behaviours, and potential token exploitation.
Have you experienced token theft in your organisation? What detection methods have you found most effective? Share your insights in the comments below.
This article is bonus content in our six-part series on phishing attacks and defences. Read Part 1: Introduction to the Blog Series, Part 2: Understanding Modern Phishing Attacks, and Part 3: Inside the Attacker's Toolkit if you haven't already, and stay tuned for the upcoming instalments leading to my presentation at the Microsoft 365 Community Conference in Las Vegas on 6-8 May 2025.