Part 1 - Modularising Logic Apps: Building Reusable Cloud Automation Solutions
Introduction
Did you know you can call Logic Apps from other Logic Apps? This powerful capability truly transforms how you build cloud automation solutions!
In the evolving landscape of cloud automation, Microsoft's Logic Apps stand out as a powerful solution for creating integrated workflows with minimal code. As these workflows grow in complexity, a well-structured approach becomes essential. This is where modularisation comes into play – breaking down complex processes into reusable, manageable components.
In this article, we'll explore the concept of modular Logic Apps that can call other Logic Apps, enabling more organised, maintainable, and scalable solutions. We'll focus on understanding the concept and exploring how this approach might benefit your organisation's automation needs.

The Benefits of Modular Logic Apps
Before diving into implementation possibilities, it's worth understanding the key benefits of modular Logic Apps. Reusability stands as perhaps the most compelling advantage – when you build a component once, you can use it across multiple workflows, saving valuable development time. Maintainability also improves dramatically, as you can update functionality in one place instead of making changes to multiple workflows.
Modularisation brings simplification to complex processes by breaking them into focused, manageable parts. This approach also fosters team collaboration, as different team members can focus on specific modules according to their expertise. Your testing regime becomes more streamlined too, as you can test individual modules in isolation before integration.
One often-overlooked benefit is the improved security posture through reduced permission scopes. When your Logic Apps are modularised, each module can operate with only the specific permissions it needs to perform its task, rather than requiring broad permissions across the entire workflow. This principle of least privilege significantly enhances your security, as it limits potential attack surfaces and reduces the impact of any potential compromise. For example, a module that only needs to read from a specific database won't need write permissions to other resources, thereby reducing risk.
The scalability of your solution improves as well – you can easily expand by adding new modules without disrupting existing functionality. Perhaps most importantly, modularisation brings clarity, offering a clearer visualisation of your workflow's logical structure.
Conceptualising a Modular Security Response Workflow
To illustrate the concept, let's consider a security incident response workflow that demonstrates how a complex security response process could be broken into logical modules for better organisation. Such a workflow might monitor Microsoft Sentinel for security incidents, retrieve incident details, add indicators to Microsoft Defender, create a formatted HTML report, and conditionally add comments to the Sentinel incident.
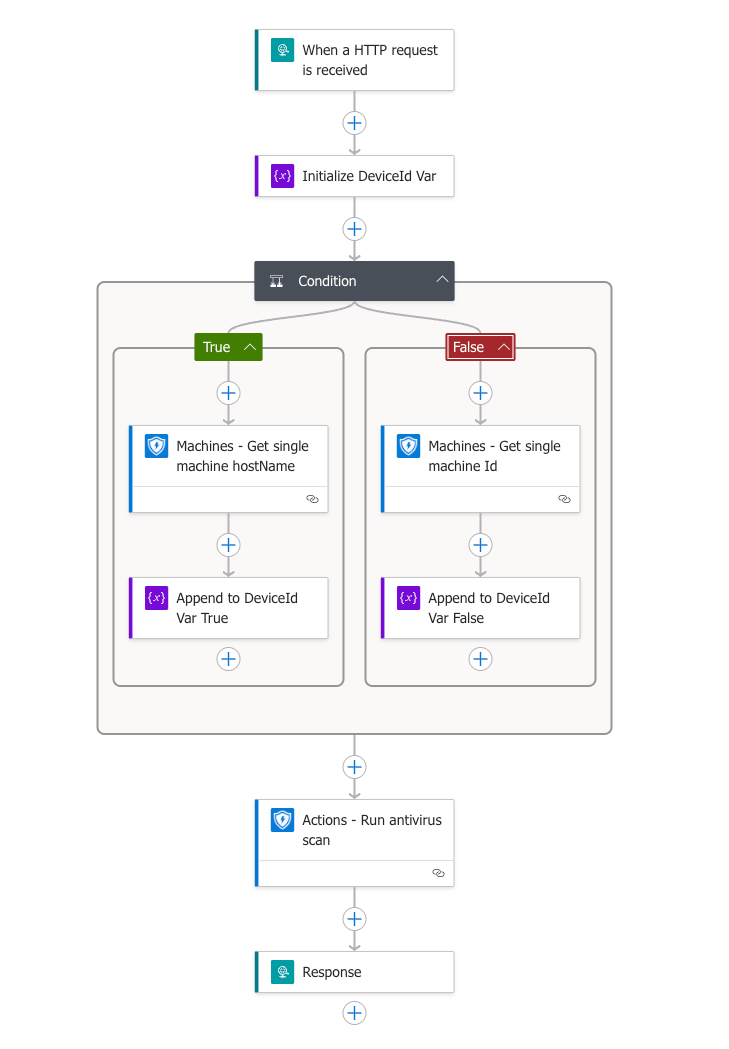
Rather than building this solution today, let's explore how we might approach designing such a workflow. The image below shows an example of what such a modular security response workflow might look like in practice:
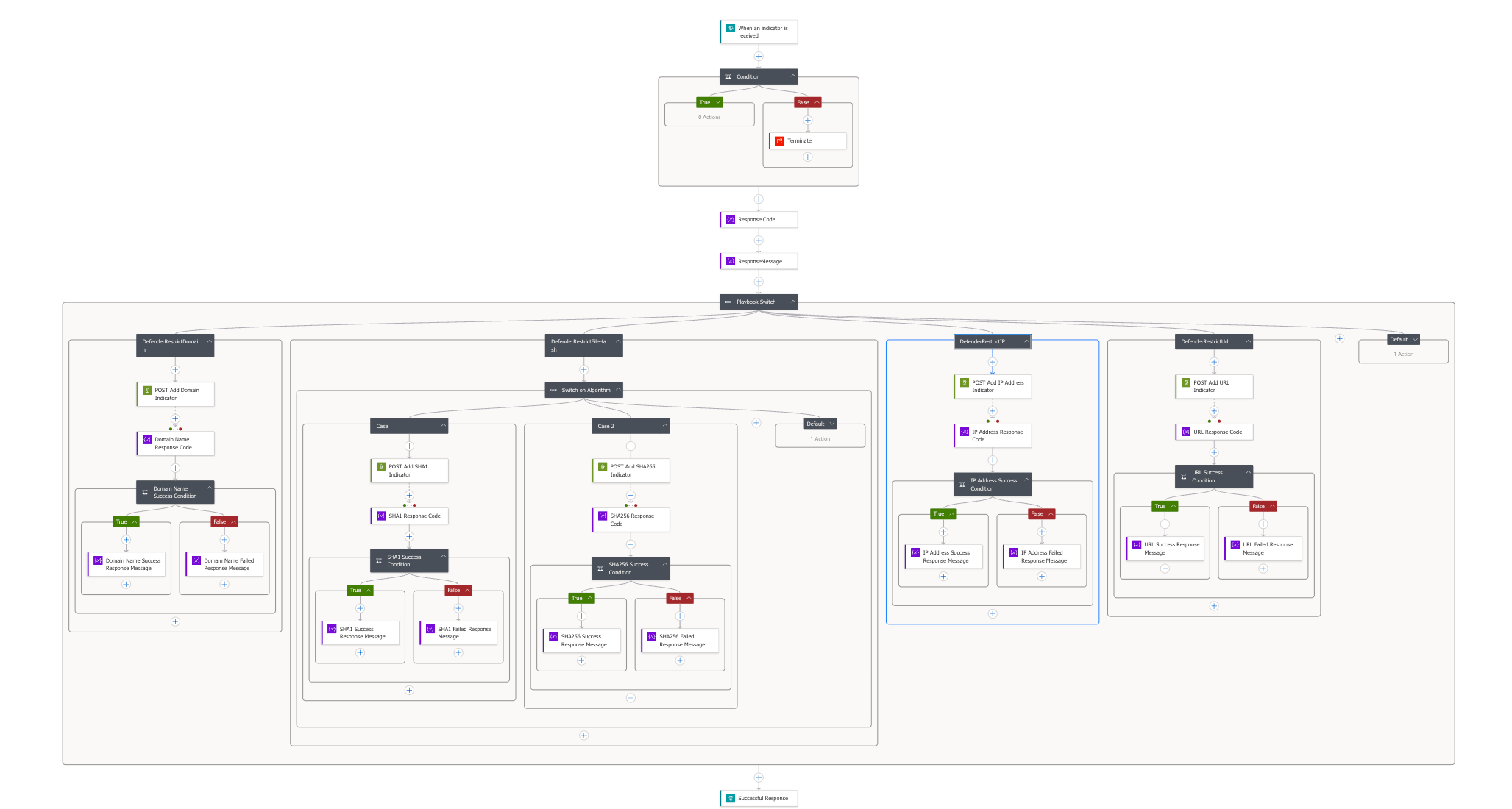
As you can see from this conceptual diagram, the solution begins with a main orchestrator Logic App at the top that handles the initial trigger and flow control. This main workflow then delegates specific tasks to purpose-built modules below it, each responsible for a discrete function.
Looking at the diagram more closely, you can see how this modular approach would handle adding different types of Indicators of Compromise (IoCs) to Microsoft Defender for Endpoint (MDE). The workflow includes separate modules for posting different types of indicators – SHA1 hashes, domains, IP addresses, and URLs – to MDE. Each module specialises in handling a specific type of security indicator, making the solution more maintainable and easier to update.
If we were to create this solution, we would begin by establishing this main Logic App that serves as an orchestrator. This app would provide a name that reflects its orchestration role (perhaps "MainSecurityResponseWorkflow"), handle the initial trigger when a security incident is detected, and coordinate the various specialised modules through a branching structure.
Our hypothetical workflow would trigger when Microsoft Sentinel detects specific types of alerts. Once triggered, it would gather comprehensive incident details and then, as shown in the flow diagram, use a parallel branch design to efficiently process different aspects of the security response simultaneously. Each branch would call a dedicated module for adding a specific type of IoC to Microsoft Defender.
This visual representation makes clear the elegant simplicity of the main workflow, which primarily consists of decision points and calls to modules, rather than complex implementation details. When designing module communication, we would need to consider how to pass parameters between Logic Apps and handle returned results, as shown by the connector lines in the diagram. This approach keeps the main workflow clean while delegating complex processing to purpose-built modules.
The Power of the Modular Approach in Practice
When considering a modular approach, we can envision how it would improve clarity in our workflows. Instead of cramming all the logic for working with various services like Defender and Sentinel into one massive workflow, we could create a clean orchestration layer that makes the overall flow easy to understand, isolates complex functionality into separate modules, and creates a more maintainable architecture.
In this paradigm, the main workflow would serve as a "conductor" that coordinates the specialised modules rather than implementing all the details itself. This approach brings several practical benefits:
- Clearer Visualisation: The main workflow becomes much simpler to understand at a glance
- Easier Maintenance: Updates to specific functionality only need to happen in one place
- Improved Security: Each module only needs permissions relevant to its specific task
- Enhanced Team Collaboration: Different team members can focus on different modules
- Better Testing: Modules can be tested independently before being integrated
If we were to implement such a solution, a consistent naming pattern such as "Module-[FunctionalDescription]" would make it immediately clear which Logic Apps are designed to be called by others. A consistent naming convention becomes crucial when working with multiple Logic Apps across an organisation.
Conclusion
Modularising Logic Apps represents a powerful approach to creating more organised, maintainable, and reusable workflows. By breaking down complex processes into logical components, organisations can create solutions that are easier to understand, test, and extend.
In this article, we've explored the conceptual foundation for modular Logic App design, examining how a security response workflow might benefit from this approach. We've discussed how a main orchestration Logic App could call specialised modules for specific tasks, improving both clarity and security.
As you consider your own Logic App implementations, think about how modularisation might help you create more elegant solutions to complex problems. The principles we've discussed—reusability, maintainability, simplification, team collaboration, improved testing, scalability, clarity, and reduced permission scopes—apply broadly across many different types of automation scenarios. The potential for creating reusable components that follow these principles is vast and worth considering for any organisation using Logic Apps for complex processes.
Stay tuned for upcoming articles where we'll move from concept to implementation, walking through the actual building process for this modular security response workflow and other practical examples of modular Logic Apps. We'll delve into the technical details of creating these modules, configuring their inputs and outputs, and connecting them to create powerful, flexible automation solutions. Whether you're addressing security scenarios like the one we've examined today or tackling other business processes, the modular approach offers significant benefits worth exploring.
I hope you've found this guide helpful in enhancing your security posture. If you've enjoyed this content and would like to support more like it, please consider joining the Supporters Tier. Your support helps me continue creating practical security automation content for the community.

