Part 4 - Building Resilient Defences with Microsoft Security: A Multi-layered Approach
Introduction
This is Part 4 of our six-part series on phishing attacks and defences. In previous instalments, we've explored various phishing attack types, examined advanced phishing frameworks, and delved into post-exploitation techniques.
As phishing attacks have grown increasingly sophisticated, with tools capable of bypassing traditional security controls, building effective defences requires a multi-layered approach addressing technical, procedural, and human elements of security.

In this fourth instalment, we'll examine comprehensive protection strategies organisations can implement, focusing specifically on Microsoft security solutions and email authentication protocols that significantly reduce phishing risks.
Email Authentication Protocols: The Foundation of Protection
Email authentication protocols form the first layer of defence against phishing by helping verify that incoming messages are genuinely from the domains they claim to be from.
SPF, DKIM, and DMARC
These three protocols work together to create a robust email authentication framework:
SPF (Sender Policy Framework) specifies which mail servers are authorised to send emails on behalf of your domain. Domain owners publish SPF records in their DNS, listing authorised sending servers, helping recipients identify and reject messages from unauthorised servers.

DKIM (DomainKeys Identified Mail) adds a digital signature to emails, allowing receiving mail servers to verify that messages haven't been tampered with and genuinely come from the claimed domain. This works through cryptographic signing using private keys, with public keys stored in DNS records.

DMARC (Domain-based Message Authentication, Reporting & Conformance) builds upon SPF and DKIM to provide enhanced protection against domain spoofing. It allows domain owners to specify policy actions for emails that fail authentication and provides reporting mechanisms for visibility.

While essential, these protocols have limitations. They don't protect against compromised legitimate accounts, can't prevent attacks using newly registered similar domains, and primarily address email-based phishing, not other channels. This highlights why email authentication must be part of a broader, layered defence strategy.

Microsoft Defender for Office 365: Comprehensive Protection
Microsoft Defender for Office 365 provides a suite of capabilities designed to protect organisations from sophisticated email threats, including phishing attacks .
Safe Links: Real-time URL Protection
Safe Links provides time-of-click verification of URLs in emails and Office documents, protecting users from URLs that initially appear safe but later direct to malicious sites.
Safe Links works by rewriting all URLs in emails and documents to route through Microsoft's security service. When a user clicks a link, it's scanned in real-time, and users are alerted when attempting to visit dangerous sites. Organisations can track which users clicked which links and implement custom block lists.

For optimal protection, enable Safe Links for emails, Office applications, and Teams, configure it to rewrite URLs in email messages, and enable the "Use Safe Links in Office applications" setting.
Anti-phishing Protection in Microsoft Defender for Office 365
Defender for Office 365 includes sophisticated anti-phishing capabilities:
Impersonation Protection detects attempts to impersonate domains and specific users, particularly executives. It uses machine learning to analyse sender patterns and detect anomalies, considering the similarity of domains and display names to legitimate senders.
Mailbox Intelligence builds a model of each user's communication patterns and identifies abnormal sending behaviours that might indicate account compromise.
Spoof Intelligence identifies sender forgery attempts, where the sender address is altered to appear as a trusted source.

For maximum protection, create targeted policies for high-risk groups (executives, finance, HR), enable mailbox intelligence and impersonation protection, and regularly review policy effectiveness.
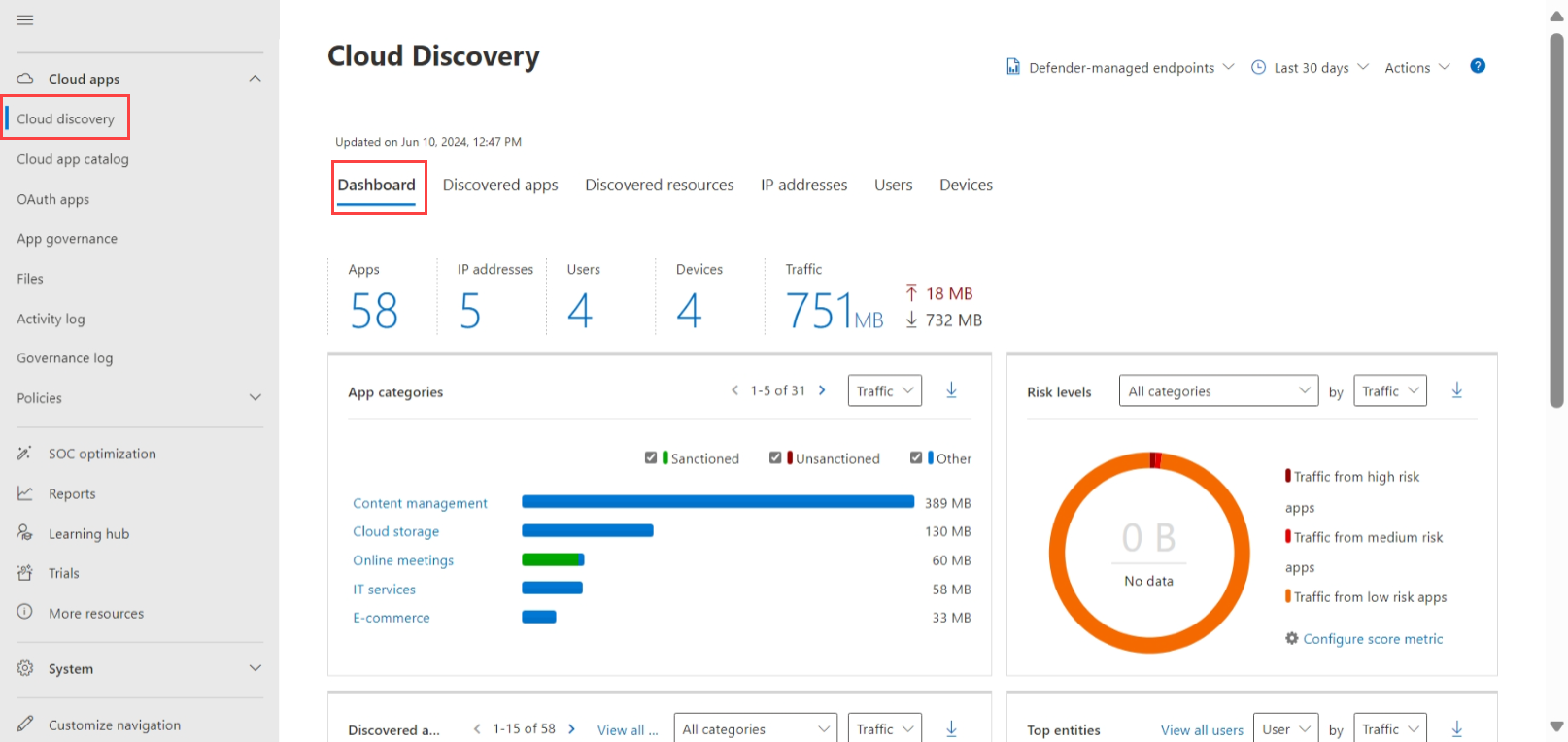
Microsoft Defender for Cloud Apps
Microsoft Defender for Cloud Apps provides visibility and control over cloud application usage as part of a comprehensive security strategy. This solution helps detect and respond to cloud-based threats, including phishing attempts that target cloud services.
Key capabilities include:
- Cloud application discovery and risk assessment
- Data protection across cloud environments
- Threat detection using user behaviour analytics
- Integration with the broader Microsoft security ecosystem

Defender for Cloud Apps can detect suspicious login attempts, unusual file downloads, or other anomalous behaviours that might indicate a compromised account following a successful phishing attack.
Advanced Conditional Access Strategies
Risk-Based Conditional Access
Risk-based Conditional Access leverages Microsoft's threat intelligence to evaluate the risk level of authentication attempts and apply appropriate access controls. When suspicious activities are detected—such as sign-ins from anonymous IP addresses, unfamiliar locations, or infected devices—additional verification can be required or access blocked entirely.
This capability integrates with Microsoft Entra ID (formerly Azure AD) Protection to:
- Detect sign-ins from suspicious locations or IP addresses
- Identify impossible travel scenarios
- Flag sign-ins from unfamiliar devices
- Require additional verification for risky sign-in attempts

Session-Based Conditional Access
Session-based Conditional Access extends protection beyond the initial authentication point to maintain security throughout a user's session. This approach is particularly effective against phishing attacks that capture initial authentication tokens.
Session controls can manage user actions once authenticated, restricting download capabilities, limiting data transfer between applications, enforcing browser isolation for sensitive resources, and applying customised restrictions based on the user's device status, network location, and calculated risk level during the active session.


Intune Device Compliance
Device compliance policies through Microsoft Intune provide an essential layer of protection by ensuring that only secure, compliant devices can access corporate resources. This helps mitigate risks from phishing attacks targeting device vulnerabilities.
With Intune Device Compliance, organisations can establish and enforce security standards for devices accessing corporate resources, verify encryption status, mandate security updates, ensure malware protection is active, and automatically remediate or restrict access from non-compliant endpoints.

When integrated with Conditional Access, device compliance becomes a powerful control point, blocking access from devices that might be compromised or lack essential security controls.
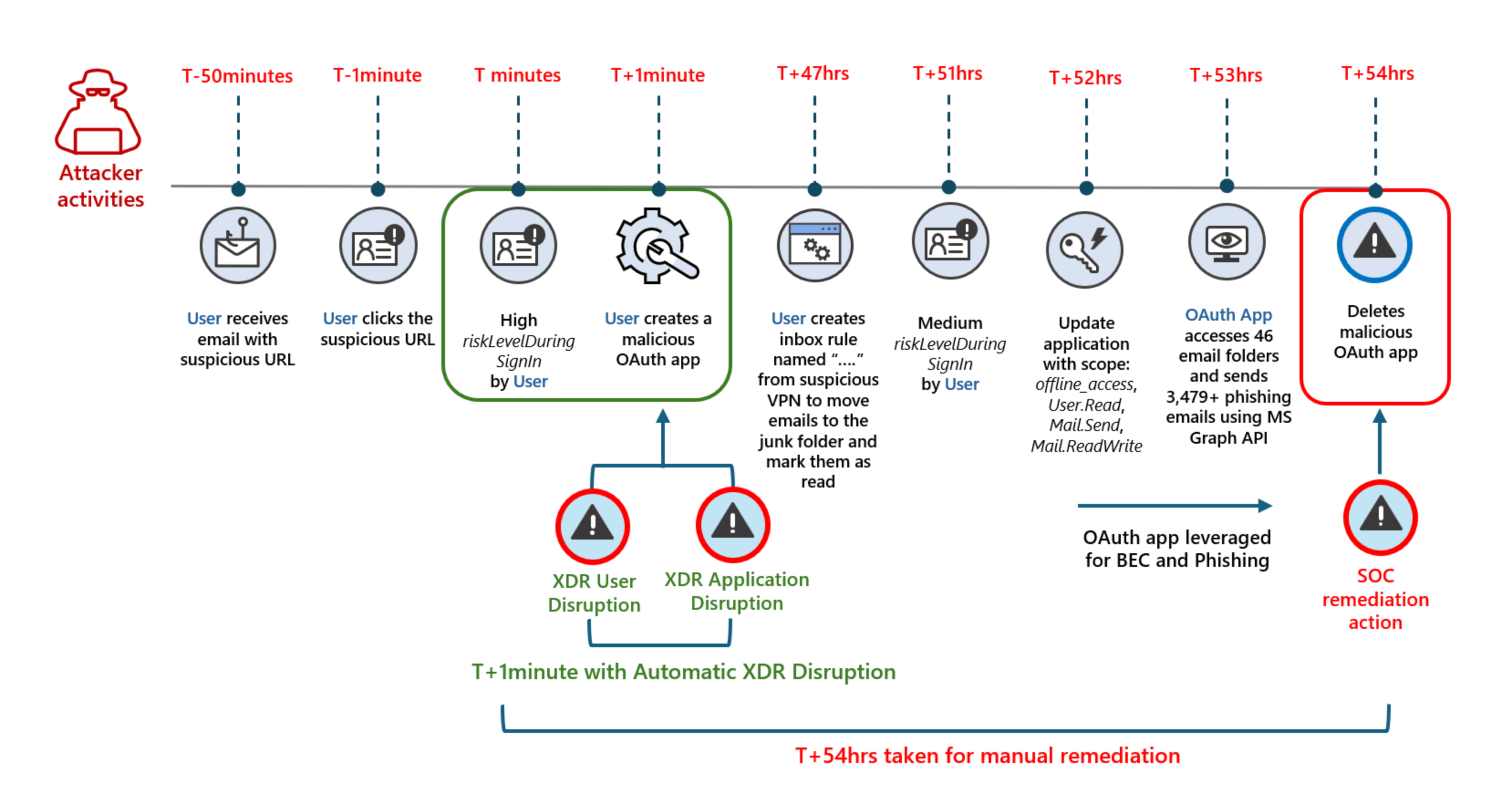
Microsoft Defender Automatic Attack Disruption
Microsoft Defender's Automatic Attack Disruption capabilities represent an advanced security approach that transcends traditional detection to actively intervene during ongoing attacks.
This technology identifies attack patterns through sophisticated correlation, implements containment measures to interrupt attack chains, quarantines compromised systems, and equips security personnel with detailed forensic information—all working in concert to reduce attacker dwell time and minimise potential damage to the organisation.
The solution works across the Microsoft security ecosystem, leveraging telemetry from endpoints, identities, email, cloud apps, and other sources to provide coordinated protection. When a phishing campaign is detected targeting your organisation, it can automatically block related emails, disable compromised credentials, and initiate investigation workflows—addressing the attack at multiple points simultaneously with minimal human intervention required.

For phishing-related incidents, this might involve automatically disabling compromised credentials, isolating affected systems, or blocking communication with command and control servers.
Building a Comprehensive Defence Strategy
Effective phishing defence requires multiple layers working together:
Prevention Layers: Email authentication (SPF, DKIM, DMARC), advanced email filtering, URL and attachment protection, web filtering, and phishing-resistant MFA.
Detection Layers: Advanced hunting queries for suspicious authentication patterns, anomalous behaviour monitoring, user reporting mechanisms, and threat intelligence integration.
Response Layers: Automated investigation and response, defined incident response processes, and continuous improvement based on lessons learned.
A Note on Comprehensive Security
It's crucial to emphasise that while the defensive measures outlined in this article provide robust protection against many phishing threats, they represent just a subset of the comprehensive security controls an organisation should implement. No single set of solutions—even when layered—can guarantee complete protection against all cyber threats. Organisations should complement these Microsoft security capabilities with additional measures such as network segmentation, privileged access management, ongoing vulnerability management, security monitoring beyond Microsoft's ecosystem, regular penetration testing, and a mature incident response capability. The threat landscape continues to evolve rapidly, and maintaining effective security requires continuous assessment, improvement, and adaptation of your defensive strategy. Remember that security is a journey rather than a destination, requiring ongoing attention and investment.
Conclusion: Building Resilience Against Phishing
The multi-layered approach outlined in this article forms the foundation of an effective phishing defence strategy. By combining Microsoft's security technologies, authentication improvements, and human awareness, organisations can significantly reduce the risk posed by even sophisticated phishing attacks.
In Part 5 of our series, we'll explore how to use Microsoft Sentinel to detect potential phishing victims through log analysis, custom detection rules, and automated response playbooks. Following that, Part 6 will examine how to implement conditional access strategies alongside phishing-resistant authentication methods.
What aspects of phishing protection have you found most effective in your organisation? Share your experiences in the comments below.
This article is part of a six-part series (plus bonus content) on phishing attacks and defences. Read Part 1: Introduction to the Blog Series, Part 2: Understanding Modern Phishing Attacks, Part 3: Inside the Attacker's Toolkit, and the bonus content on token theft if you haven't already, and stay tuned for the upcoming instalments leading to my presentation at the Microsoft 365 Community Conference in Las Vegas on 6-8 May 2025.











