Automating Entra ID App Registration Credential Monitoring: A Complete Solution
Credential Watch: Stay Ahead, Stay Secure
Published on 10 March 2025
Introduction
For any organisation using Microsoft's cloud services, EntraID (formerly Azure AD) App Registrations and service principals are crucial components of your identity infrastructure. These applications often rely on secrets or certificates for authentication, which inevitably expire. Failing to track these expirations can lead to unexpected service outages, emergency remediation work, and potential security vulnerabilities.
Today, I'm excited to share a comprehensive solution for automating the monitoring of expiring credentials in EntraID App Registrations, complete with proactive email notifications to ensure your team stays ahead of potential issues.
The Problem: Credential Expiry Management
Managing application credential expiry in EntraID presents several challenges:
- Visibility: No built-in dashboard shows all expiring credentials across your tenant
- Scale: Manual checking becomes impractical as your application portfolio grows
- Proactive management: Reactive approaches often lead to fire-fighting and service disruptions
- Operational overhead: Security teams need automated solutions to reduce manual tracking
The Solution: Automated Monitoring and Notification
Our solution combines Azure Automation with Logic Apps to create a robust monitoring system that:
- Regularly checks all EntraID App Registrations for expiring credentials
- Identifies both expiring secrets and certificates
- Formats the data in a comprehensive, easy-to-read format
- Delivers elegantly formatted email notifications to your security or operations team
Let's break down each component of this solution.
Solution Architecture
The solution consists of two primary components:
- Azure Automation Runbook: A PowerShell script that connects to Microsoft Graph, retrieves application data, and identifies expiring credentials
- Logic App Workflow: Receives the payload from the runbook and transforms it into a well-formatted email notification
Component 1: PowerShell Runbook for Credential Monitoring
The PowerShell runbook handles the heavy lifting of credential discovery and analysis. It:
- Connects to Microsoft Graph using a system-assigned managed identity
- Retrieves all App Registrations in your EntraID tenant
- Checks both password credentials (secrets) and key credentials (certificates) against a configurable expiry threshold
- Creates a standardised JSON payload containing all necessary information
- Posts this payload to a Logic App for notification processing
Here's the core of the runbook that checks for expiring credentials:
The script produces a flat JSON structure that makes it easy to process and display the results.
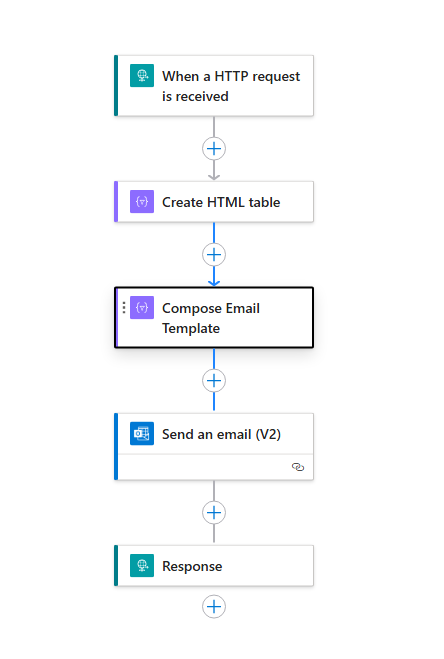
Component 2: Logic App for Email Notifications
The Logic App workflow takes the JSON payload from the runbook and transforms it into a visually appealing email notification. The workflow:
- Receives the HTTP request containing expiring credential data
- Creates an HTML table from the received data
- Embeds this table into a professionally designed email template
- Sends the email to designated recipients
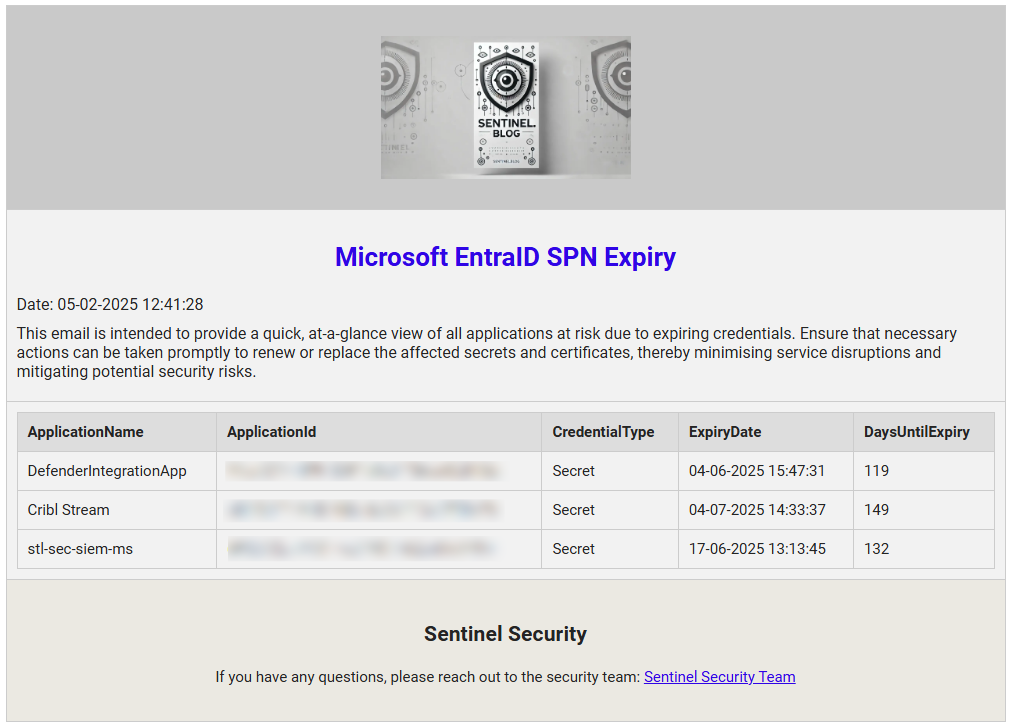
The Email Template
The email notification is built using a responsive HTML template that presents the information clearly across desktop and mobile devices:
![Email Template Screenshot]
The template includes:
- A professional header with organisation branding
- Clear explanation of the notification purpose
- A neatly formatted table showing:
- Application name
- Application ID
- Credential type (Secret or Certificate)
- Expiry date
- Days until expiry
- Status (Expired or Expiring Soon)
- Contact information for the security team
The CSS styling ensures that columns maintain appropriate widths and that the table remains readable even when displaying numerous entries.
Setting Up the Solution
Prerequisites
- An Azure subscription with access to:
- Azure Automation
- Logic Apps
- Appropriate Microsoft Graph permissions (Application.Read.All) for the Automation Account's managed identity
- Required PowerShell modules in your Automation Account:
- Microsoft.Graph.Authentication
- Microsoft.Graph.Applications
Implementation Steps
- Create the Azure Automation Runbook
- Create a new PowerShell runbook in your Automation Account
- Paste the provided script code
- Configure the system-assigned managed identity
- Assign the necessary Microsoft Graph permissions
- Set Up the Logic App
- Create a new Logic App with an HTTP trigger
- Configure the HTTP request body JSON schema
- Add an action to create an HTML table from the incoming data
- Add an email action using the provided HTML template
- Configure email recipients
- Schedule the Solution
- Set up a recurring schedule for the runbook (e.g., weekly)
- Test the end-to-end workflow to ensure proper functionality
Security Considerations
When implementing this solution, consider the following security best practices:
- Use managed identities instead of service principals or credentials whenever possible
- Apply the principle of least privilege when assigning permissions
- Secure your Logic App endpoints with IP restrictions or Azure AD authentication
- Encrypt sensitive information in transit and at rest
- Regularly review and audit your automation for security improvements
Conclusion
The EntraID App Registration credential monitoring solution provides an elegant and effective approach to managing credential expiry across your Microsoft cloud environment. By automating this critical operational task, your team can focus on more strategic initiatives while ensuring that credential renewals happen proactively, preventing service disruptions and minimising security risks.
This solution demonstrates how PowerShell, Azure Automation, and Logic Apps can be combined to create practical operational tooling that addresses real-world challenges in managing cloud identities securely.
Have you implemented automation for credential management in your environment? Share your experiences in the comments below!
I hope you've found this guide helpful in enhancing your security posture. If you've enjoyed this content and would like to support more like it, please consider donating to the tip jar. Your support helps me continue creating practical security automation content for the community.